Malware authors have hijacked DNS settings on vulnerable routers to redirect users to sites hosting Android malware.
According to Kaspersky Labs telemetry data, these were small-scale attacks, as crooks only hijacked traffic from just 150 unique IP addresses, redirecting users to malicious sites around 6,000 times between February 9 and April 9, 2018.
But while researchers weren’t able to determine how crooks managed to gain access to home routers to change DNS settings, they were able to get their hands on a sample of the Android malware used in these attacks —an unique strain they named Roaming Mantis.
CROOKS HID MALWARE IN CHROME AND FACEBOOK CLONES
For these attacks, crooks redirected users to pages peddling clones of Android apps like Google Chrome for Android (chrome.apk) and Facebook (facebook.apk).
Both the websites hosting the fake apps and the apps themselves were available in five languages —Korean, Traditional Chinese, Simplified Chinese, Japanese, and English.
These apps used excessive permissions, allowing them total access to the users’ smartphones. The apps’ main purpose was to overlay login screens on top of various apps.
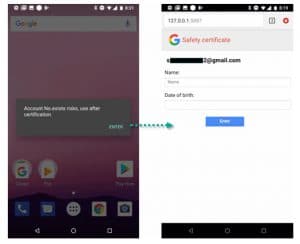
Researches said the malware was hardcoded to target popular games and mobile banking apps from South Korea. Suguru Ishimaru, a security researcher for Kaspersky, said most of the victims were located in South Korea, Japan, India, and Bangladesh, and that Korean was also the primary language of the web pages and inside the malicious apps.
Based on his analysis, Roaming Mantis appears to be an information stealer, as the malware’s source did not contain any code that attempted to exfiltrate funds from users’ accounts, albeit the stolen credentials could be used off-device to commit fraud later on. More details about Roaming Mantis are available in a Kaspersky Lab report.
ROUTERS BECOMING MORE POPULAR WITH MALWARE AUTHORS
But while its source code is nothing spectacular or out of the ordinary, its distribution method —of hijacking DNS settings on home routers— is something that has not seen before with Android malware.
The use of compromised routers for malware distribution fits a recent trend where hacked routers have become the favorite playing ground of IoT botnets, proxy networks, and cyber-espionage groups.